1Password SSH Integration

Tower provides seamless integration with 1Password, a popular password manager application, which also supports managing your SSH keys and use them for authenticating SSH remote connections and SSH commit signing.
1Password comes with its own SSH Agent implementation that can be used by other applications to list and access all SSH keys that are stored within 1Password.
Enabling the 1Password SSH Agent
Before you can use any of the 1Password SSH features in Tower (or any other external tool), you need to enable the 1Password SSH Agent in 1Password's Settings, under the “Developer” item, and adjust its settings to your needs.
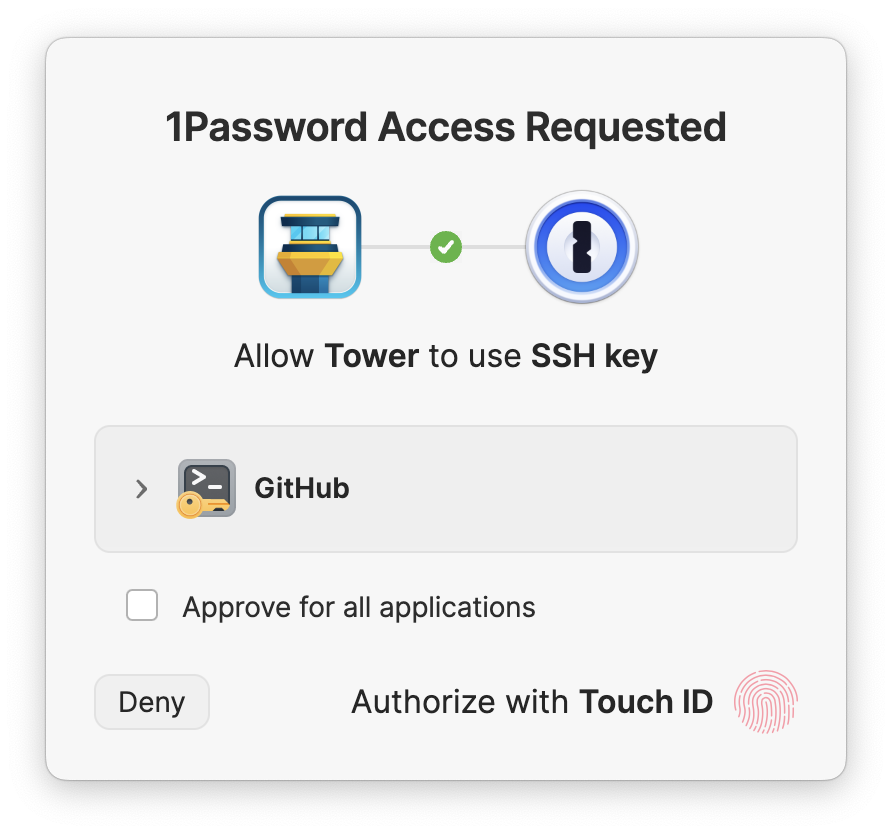
Once the 1Password SSH Agent is up and running and you have chosen to use it for authenticating SSH remote connections in Tower as per one of the options described below, the next time you invoke an SSH remote operation, like “Fetch”, a 1Password prompt will show to confirm access and allow Tower to use the SSH key for the connection.
Depending on how the 1Password SSH Agent is configured, you will be prompted for confirmation again from time to time.
The same prompt will show up when using the 1Password SSH Agent for signing commits or tags with an SSH key.
Using 1Password for authenticating SSH remote connections in Tower
There are two options to use the 1Password SSH Agent for authenticating SSH remote connections in Tower. Which one to choose might depend on your specific use-case or preference.
1. Using IdentityAgent in your SSH configuration
On macOS, the default location for the SSH configuration is ~/.ssh/config. If your ~/.ssh folder or config file doesn't exist yet, you need to create it first.
Add the following snippet to your ~/.ssh/config file:
Host *
IdentityAgent "~/Library/Group Containers/2BUA8C4S2C.com.1password/t/agent.sock"This will set the 1Password SSH Agent for SSH connections to any host by default. If you wanted to use the 1Password Agent for only certain hosts, you can add specific values for the Host entry:
Host customdomain1.com customdomain2.com
IdentityAgent "~/Library/Group Containers/2BUA8C4S2C.com.1password/t/agent.sock"In Tower, there is nothing else to configure with this option, as Tower simply invokes Git commands and Git will automatically use the system SSH configuration just as it does on the command line.
About using IdentityAgent
This will change your system-wide SSH configuration and will therefore affect all SSH connections that make direct use of it. This can be the preferred option if you want to use the 1Password SSH Agent in multiple applications using SSH connections.
2. Override SSH Agent environment variable
An alternative approach is to override the SSH Agent through an environment variable offered by SSH.
On the command line, you would do it as follows:
export SSH_AUTH_SOCK=~/Library/Group\ Containers/2BUA8C4S2C.com.1password/t/agent.sock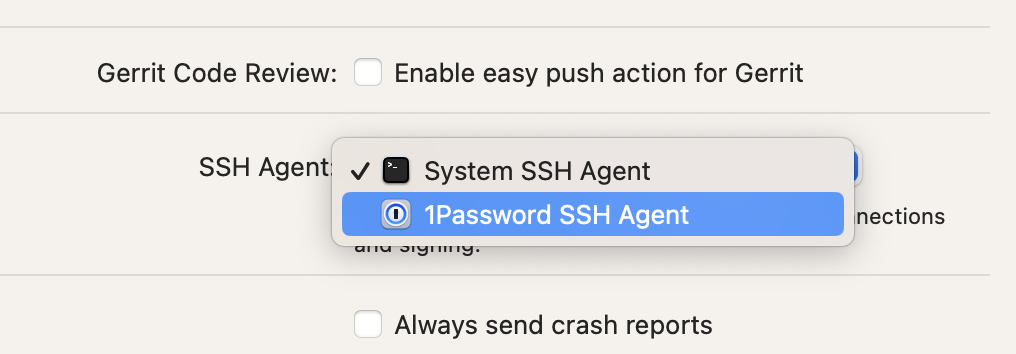
To achieve the same in Tower, simply select the 1Password SSH Agent on the “Integrations” tab in Tower's Settings and it will be used as the default SSH Agent for SSH connections.
About overriding the SSH Agent environment variable
Overriding the SSH Agent will always affect both SSH remote connections and SSH signing.
Using 1Password for signing commits and tags with SSH keys
To access your SSH keys stored in 1Password from Tower for signing commits and tags, there are two options again.
1. Configure gpg.ssh.program to use the 1Password signing helper program
Git offers the configuration variable gpg.ssh.program to set a program that is used when signing or validating commits using an SSH signature.
Add the following section to your global Git config:
[gpg "ssh"]
program = "/Applications/1Password.app/Contents/MacOS/op-ssh-sign"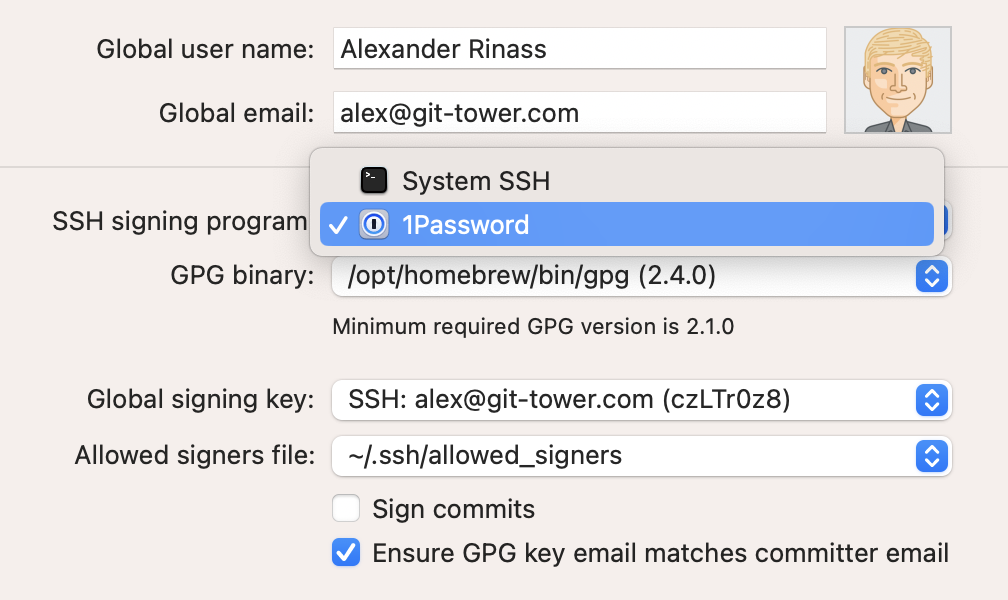
In Tower, you can make the same change by selecting “1Password“ as SSH signing program.
If 1Password has been selected, the “Global signing key“ drop-down will list all available SSH keys provided by the 1Password SSH Agent. Select a key, enable “Sign commits” and the next time you commit you will receive the 1Password prompt as displayed at the beginning of this article.
2. Override SSH Agent environment variable
This is the same approach as outlined above for using 1Password for authenticating SSH remote connections.
If the 1Password SSH Agent is configured in Tower, the “Global signing key“ drop-down will automatically list all available SSH keys provided by the 1Password SSH Agent and also used when signing commits with SSH.
About overriding the SSH Agent environment variable
Overriding the SSH Agent will always affect both SSH signing and SSH remote connections.